- Georgia Computer Inc.
- Services
- IT Asset Disposition
IT Asset Disposition

ITAD Services
GCI is your trusted ITAD provider. We are committed to responsible disposition of electronic assets to protect the earth and continue to make the world a better place.
Data is one of your company’s most valuable assets. You jump through a series of protective digital hoops, knowing that each security measure is necessary for the end goal—to safeguard your data and your brand.
But what happens when you start decommissioning redundant equipment and recycling EOL hardware? Each IT device from servers to smart phones presents both a data security risk and a hazard to the environment. Data security responsibilities do not end with the retirement of obsolete units. In order to protect your customers and your business, residual data should be secured with the same dedication.
Data breaches are kryptonite to your company brand. A breach can result in legal liability, declining customer confidence, and loss of professional credibility.
You need to safeguard both your customers and your reputation with security protocols until there is no data left to secure. Unfortunately, most companies lack the correct tools to execute effective and environmentally sound IT asset disposition (ITAD) measures in-house. That’s where certified vendors such as GCI come in.
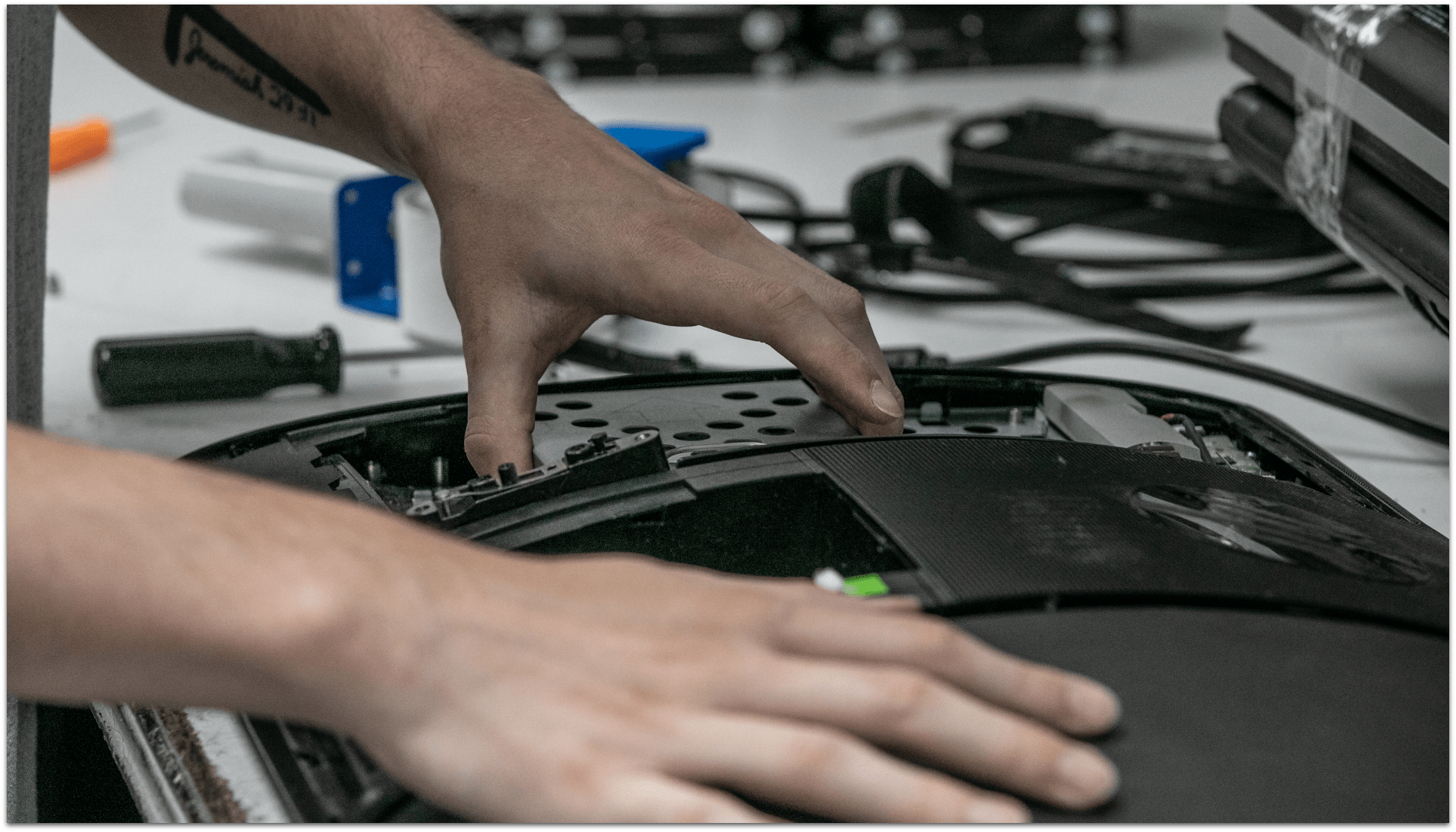
FEATURED SERVICES
IT Asset Disposition
ITAD services complete the lifecycle of end-to-end data security, deleting data and disposing of unwanted IT equipment in a safe, effective and environmentally accountable way. GCI is committed to responsible disposition of electronic assets. We provide proven expertise in both protecting the earth and mitigating client risk.
Secure Logistics & Transport
The secure handling of data is one of the most important aspects of ITAD. Once an IT asset is removed from an organization’s network, it is at higher risk for breach. GCI is committed to the protection of your assets from the moment they leave your facility until they arrive at ours.
- We can send our truck to your location, pack up your equipment and transport to our warehouse ensuring the secure chain of custody.
- Secure chain of custody means no information will be compromised.
- Once in our warehouse, all equipment is audited and an inventory is created.
- All equipment is wiped of all information.
- A certificate of compliance is provided to the customer along with the audit report so there is a paper trail and accounting of all equipment.
- GCI ensures that data-bearing devices are sanitized safely and properly using methods aligned with NIST 800-88 guidelines. Drives that cannot be sanitized are degaussed and destroyed to prevent data recovery.
- GCI is committed to the highest level of information security. In addition to the tools above, our lab and tech room are under 24/7 CCTV video surveillance. Furthermore, GCI carries a $5,000,000 Technology, Cyber, and Data Risk insurance policy to give our clients added peace of mind.
Remarketing/Reuse
- We have many buyers/relationships in the secondary market and source and resell hardware all over the world every day.
- We resell to our global customer base
Recycling
- GCI is an R2/RIOS Certified Electronics Recycler assuring the safety and proper handling of all electronic equipment.
- As an R2/RIOS certified company, we follow the strictest standards of equipment and materials management. GCI uses the “Reuse, Reduce, and Recycle" process.
- Responsible e-waste recycling from GCI guarantees that your equipment will not end up in a landfill.
- GCI complies with and exceeds all EPA regulations and guidelines for handling e-waste and other hazardous materials.
- We disassemble each item and sort it into core components, metals, and non-metals. We then recycle each commodity so it can be used in the manufacturing of new goods.
- Any non-functioning drives are put through our Garner HD-3WXL Data Eliminator. After being degaussed, the drives are then put through our Garner PD-5 crusher to be destroyed and recycled.
- All PDA devices, cell phones, tablets etc. that cannot be successfully overwritten will be destroyed via our Garner PD-5 crusher and then recycled properly.
- We are also capable of using both the Wipe OS and PD-5 Crusher to wipe/destroy hard drives onsite.
Reporting
- Using our proprietary management system, GCI provides our clients with a detailed audit of all equipment we handle and can fulfill special reporting requests as needed.
- When received at GCI, all equipment (PC’s, laptops, POS equipment, servers, printers etc.) are given a lot number. The equipment is then audited to capture all serial numbers, including Category, Brand & Model
- Configurations (COA , CPU, GEN, Ghz, HDD Size, RAM & ROM)
- All asset tags identifying the owner of the equipment will be removed and destroyed prior to recycling or remarketing.
- Once this audit is complete, the audit is sent to the customer along with hard drive wiping reports and certificates of compliance.
